Using the C-I-A triad to value assets
In many security activities, you need a way to prioritize assets. A simple and widely used approach is to evaluate assets through the CIA triad:
- Confidentiality: what happens if sensitive information is disclosed?
- Integrity: what happens if the data is modified or tampered with?
- Availability: what happens if the system or data is unavailable?
By scoring assets against these three criteria, you can arrive at an overall rating that reflects their criticality.
C-I-A Score
I typically call this CIA score but I have seen this refeered to by many names, such as:
- Security Category (From NIST’s FIPS-199 which I think was the earliest document I could find containing this concept)
- Asset Risk Score
- Asset Value
- Asset Rating
- Asset Security Score
So if you are new to this and are looking to implement something like this in your ISO 27001 implementation or your security program, I am presenting two approaches here.
In both the asset owner evaluates what happens to the company when there is a violation to one of the C-I-A triads.
You can explore this using the simple tool. Below the tool you can find how this final outcome will look like in an asset register.
Tool
The first model in the tool is directly based on the approach in FIPS-199 where as in the second I have used a weighted score approach.
Using the score in an Asset Register
Here’s a fictitious example generated using ChatGPT where assets are scored using the second Weighted approach in the tool.
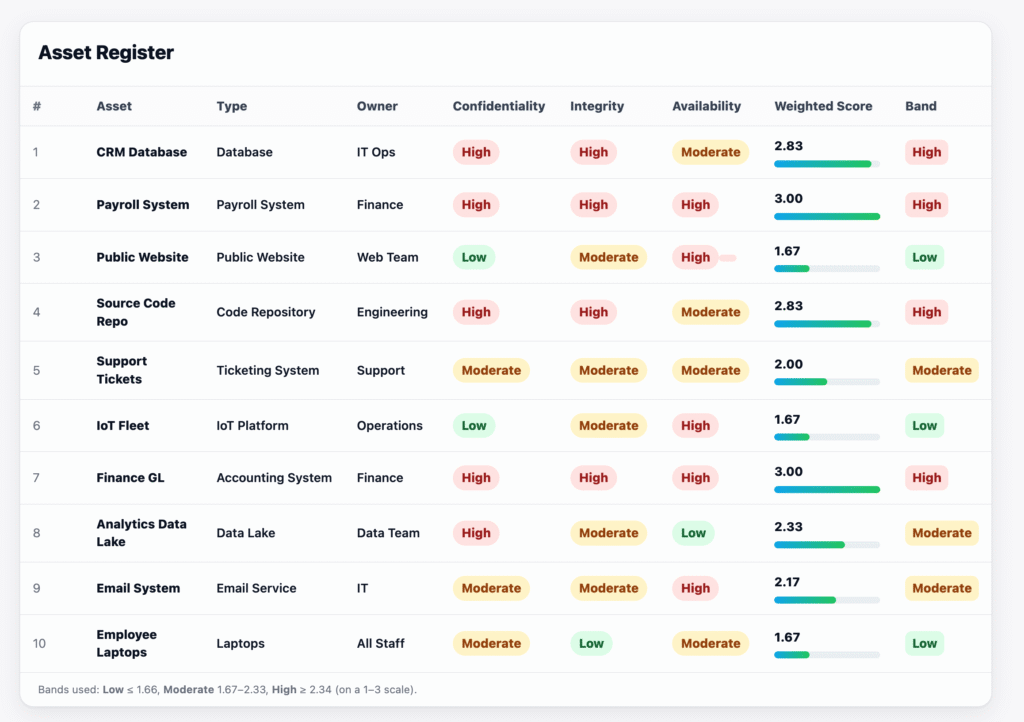
This kind of table makes it easy to rank assets by importance. Once you have a ranked list, your crown jewels should (ideally) appear at the top.
Such ranked assets can also be used when you have a big project (implementing a new control organization wide). Assets that appear at the top could be one factor to consider when you decide the phases.

